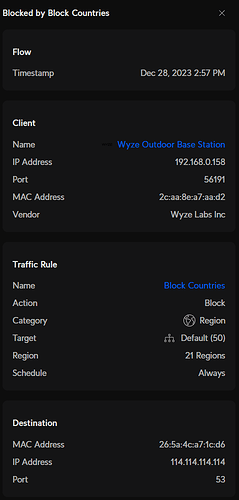
Early this morning I was reconnecting my outdoor base station and cameras which all needed firmware updates. I had the previous day also did some firmware updates. These cameras had been offline since I had a concern of a breach at my home. My router blocked activities coming specifically from my Wyze Outdoor Base Station, twice. Does anyone know if Wyze uses a specific China IP address for firmware updates or similar. See below my notice. My Base Station Mac Address attempted twice to connect with 114.114.114.114.
You could email security@wyze.com
If this is an issue, they would be able to let you know
Yeah, totally email them, and let us know what they have to say. That IP is a mobile communication company in China, so im very, very doubtful its an IP for anything Wyze (even with that info tech inc. title). Remember China is the two states one system country, so every company operating in that country is beholden to the China Authorities, which absolutely includes spying, and/or obtaining any data a company has.
IP Info:

Id also recommend going into your router and enabling geo-blocking by country, and including China (and any others you want) in the block. Of course they can have a VPN or server in another country, but block the obvious first. Glad your router/firewall spotted that.
let us know how it goes, DeVoiD
Its a DNS server in China. That needs to be taken out of the base station’s code.
here, this tells of that IP address: https://www.reddit.com/r/EufyCam/comments/hdyyy4/do_you_trust_eufys_security/
Why would it have a Chinese DNS server IP address, hardcoded - has to be as it would get DNS from the routers DHCP - in the base stations programming??? we have plenty of DNS servers in the US (and around the world), plus the one our ISP assigned our internet modems.
Anything to say on this Wyze people?
That IP needs to be removed from any and all code.
DeVoiD
I also just started to get the same notification on my router from my Wyze hub. It just started two days ago and I have not updated the firmware recently. 4.16.2.66 is my current firmware. I submited a log but I will also send the information to Wyze security.
Has there been a response from Wyze?
Wyze Cybersecurity responded to me that they duplicated the issue and alerted thier firmware team internally. The behavoir is to be fixed in the next firmware update. They referenced that “The DNS Queries will be limited to US servers only.” I appreciate their quick response, however, I am now concerned that no one in their US team is reviewing the firmware code. I was comfortable with Wyze because they were founded in the US from Amazon employees. I assumed even though they sourced out of China, they did their own code review. I am no expert, so now I have a bit of concern.
I may have to setup a VLAN isolation on their products that require ethernet and move all of their Wifi products to my “Guest Wifi” as well. I hoped to avoid that given no one else in my household will have any idea what is going on when things go wrong. Does anyone else do any network logging of thier Wyze products such that we as a group can feel more comfortable?
Go into your router/firewall, and just block the IP by inbound/outbound, or a lot of routers/firewalls have a geo-block and so you can just block China and any other country you are worried about. being its a DNS server that will be static to the country, and isnt likely to get hosted in another country, so blocking like that will work.
I didnt realize the actual programming of the app was in China, I thought it was coded in the US… that is worrying… especially given that that China hardcoded that IP into the devices in a fairly (to IT people) obviously easy way to find, they could quite easily create a more complex and hidden code into it, making it less obvious, including an IP to a server in the US which they can access via VPN and that in turn sends data back to home-base in China.
After the next firmware, it would be great if you all posted back to see if your router/firewall sees that IP again, so we know it was taken out of the code. The problem though, goes back to how China operates, every company there is beholden to the state and if they want to stay in business they have to do what their masters tell them too. So im concerned that there will be a well hidden bit of code that does a heck of a lot more than DNS queries…
Seriously re-thinking my purchasing decision (im many hundreds of $'s into their eco-system)…
Ill say one thing, im going to turn off everything wireless except for my base station and cameras, and then im going run Wireshark against every packet going across my home network, and even though it will be a vast amount of data (maybe ill only use my base-station, one outdoor camera and my pan-cam) ill let it run for 24 hours, as who knows, maybe its set to do something at a specific time (it knows your location, maybe habits like going to bed and runs it when it knows you are in bed or out of the house), and by running for 24 hours it might capture other things… again, thats a ton of data though to sift through! DeVoiD
Good find on the Eufy forum post but even there the poster dismisses it as a serious concern.
I have it on a network protected by a Cisco Firepower firewall, Meraki wireless and security monitoring tools for DNS and Netflow. Overall I haven’t seen any huge red flags. It is hard coded to do certain DNS queries against a Chinese DNS provider (114.114.114.114) but I NAT those queries to my own DNS service and the lookups themselves are benign. Pretty much everything is hosted in US AWS and I’ve seen zero evidence of it shuffling video content out of my home (I stream exclusively using HomeKit Secure Video and never use the Eufy app remotely).
If I had to guess it would be that Chinese programmers use that IP address for ready DNS just as US programmers use 8.8.8.8 (Google DNS) - because it’s available and easy to remember.
The code review is a different and valid question. We’ve seen other interesting behavior, such as excessive DNS queries and overly persistent P2P connections.
There are lots of things that can be done with DNS, dont forget that. how about malicious redirects, or “man in the middle attack” for starters. So while they might blow it off as not terrible, it has the potential of being really bad, and if you have control of that DNS server (which of course the Chinese government has), its worse.
just a brief of the 5 common hijacks/attacks via DNS:
yeah, its bad, and even if its not misused, it could so easily be by their government.
DeVoID
You’re right. Widespread TLS mitigates it a bit, but foreign control of your DNS is not good.
First, I want to acknowledge and applaud Wyze’s openness to answer my questions and quick responses.
Here is the latest response, but I am not sure it addresses my concerns. They did address that thier Firmware team is US based and internal. As to why they were not aware of the DNS code directing to China and why if they don’t sell into the China market they would have that code in the first place. Finally, I am not sure how the fact that they encrypt helps me in this situation where my Base Station is sending a direct request to a Chinese fixed IP address. I would imagine the DNS provider now knows my IP address and the fact that I have Wyze devices at that address.
> We completely understand your concern. At Wyze, we take Customer Data Privacy and Security very seriously. Yes, our firmware team is based in Seattle, WA. Also, we only sell Wyze products in the USA and Canada.
*> *
> The communication requests between your mobile device, your Wyze product, and the AWS Cloud Server are made via https (Transport Layer Security (TLS)) for Event videos. We use symmetric and asymmetric encryption, consistent hashing, and other ways to make sure users’ information cannot be stolen. Each camera has its own secret key and certificate so that we can validate its identity during handshake. The contents are encrypted via AES 128-bit encryption to protect the security of the live stream and playback data. During the connection process, every device in the process has its own secret key and certification, so that we can validate their identity during handshake. Even if a hacker intercepts the data package, the data cannot be decrypted.
Well, you know, except that DNS queries are very, very rarely encrypted.
After yesterday the blocked DNS all of sudden stopped being detected on my router. That is after I was getting 10 -15 a day when it first started. Seems strange since they said it was going to be a firmware fix.
Did you confirm that your firmware did not get an update? I have had mine unplugged since that day, so I am unaware if there is an update out there. Wyze keeps telling to make sure I update my firmware, but I thought it said it was on the latest firmware.
I got bold and decided to try to go to the IP address on a burner laptop. Here is what MCAFEE had to say about it.
No firmware update, just stopped trying to get there.
In fairness, McAfee is mostly garbage though.
Some search hits about the address.
https://blog.karatos.in/a?ID=01500-111438d2-d1fe-4562-9b2e-986a90fcdbe5
Wyze still should have caught this and changed it of course.
Sure, everyone can take a stab at all of the antivirus software that is out there, but I did not want to pick a company that is out of Russia, or Czech Republic, Romania or etc. given the current political times. I thought having something is better than nothing as long as it did not cause issues with my devices, which so far has been surprisingly smooth. Anyway, I have not plugged my base station in for now until I hear there is a firmware update or I connect it to VLAN/Wireless guest (running it on wifi is not a good solution).
If it really is just that one address then you can probably block it at your router…